Bitchat: Bluetooth Mesh Networks and Internet Shutdowns
By Tom Everill | 27 January 2026
Summary
Bitchat enables short-range, decentralised messaging during internet shutdowns using Bluetooth mesh networks.
It has seen rapid protest-driven uptake recently in Uganda and Iran amid government-imposed blackouts.
Experts warn it remains vulnerable to surveillance, technical flaws, and state countermeasures.
Context
On 6 July 2025, Twitter (now X) founder Jack Dorsey posted on X about a weekend project to ‘learn about Bluetooth mesh networks’ while sharing a link to a beta version of his new app, Bitchat.
Bichat is a decentralised peer-to-peer messaging app which connects users using Bluetooth Low Energy Mesh Networks rather than relying on traditional telecommunication infrastructure. By sidestepping centralised networks, the platform can facilitate communication amid internet blackouts. It requires no account or phone number and claims to offer end-to-end encryption.
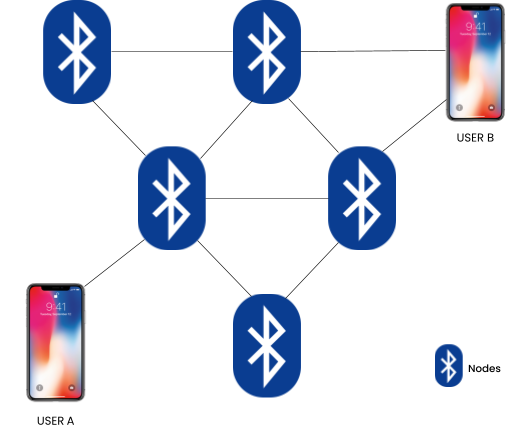
The above diagram illustrates how messages in a Bluetooth mesh network hop from one nearby device (node) to another, rather than travelling directly over the internet. User A’s message is passed along through multiple Bluetooth-enabled devices within range until it eventually reaches User B.
Bluetooth’s technical limitations naturally restrict the range of such platforms. Dorsey claims Bitchat is functional up to 300 metres, well beyond the standard, roughly 100 metres achieved by competitor products. This means that while the app cannot facilitate offline messaging city, nation or world-wide, it excels in providing connectivity in dense environments with poor or absent internet connection, like music festivals or protests.
Use Amid Protests & Internet Blackouts
This latter use case has attracted recent attention amid internet blackouts in Uganda, ahead of its 15 January 2026 Presidential Election, and in Iran, as anti-government protests spread nationwide in early 2026. However, the use of Bluetooth messaging during protests is not new. A similar app Bridgefy was used during Hong Kong’s 2020 pro-democracy demonstrations to bypass internet restrictions and state surveillance (although its effectiveness in the latter is contested), and Bitchat itself has also seen recent use in Nepal’s ‘Gen-Z Protests’.
Skepticism & Risks
Despite its decentralised design, experts caution against assuming Bitchat is imperceptible to state surveillance. Professor Alan Woodward of the University of Surrey told the BBC that peer-to-peer networks still generate rich metadata. Even if message content remains encrypted, capable authorities can monitor which devices communicate, when, and in what patterns. This is often sufficient to identify organisers or map protest networks.
Others warn of active counter-measures. Ziya Sadr, a former Iranian political prisoner, highlights phishing campaigns, fake download links, and paid social-media influencers pushing compromised versions of protest apps. These risks are heightened during blackouts, when users are forced to sideload software with limited means of verifying that installed versions match the original audited code.
Moreover, Bitchat remains technically immature. Security researcher Alex Radocea identifies serious vulnerabilities including the potential for ‘man-in-the-middle attacks’ stemming from weak identity authentication, allowing attackers to impersonate trusted contacts. The app also lacks robust forward secrecy: encryption keys remain static for entire sessions, rather than refreshed per message, as in more mature secure messengers. These issues are compounded by the app’s limited exposure to prolonged hostile scrutiny in real-world situations.
Overall, many commentators urge protesters not to treat Bitchat as a silver bullet. While it may be useful in specific contexts, overselling its “censorship resistance” risks encouraging unsafe behaviour. Layered communication strategies, realistic threat modelling, and clear communication of residual risks remain essential in high-risk environments such as Iran and Uganda.
Forecast
Short-term (Now - 3 months)
Further spikes in Bitchat (and forks) downloads are likely during election-related unrest and internet shutdowns, particularly in authoritarian contexts.
Governments are likely to issue public warnings, threaten bans, or experiment with Bluetooth detection and disruption rather than fully suppressing usage.
Medium-term (3-12 months)
State countermeasures (phishing, compromised forks, legal deterrence, and metadata exploitation) are likely to reduce the app’s perceived safety among high-risk users.
Without rapid security hardening and clearer threat modelling, Bitchat risks being relegated to niche or low-risk use cases rather than sustained protest coordination.
Long-term (>1 year)
Bluetooth mesh messaging is likely to persist as part of a broader “resilience stack” for activists, rather than a standalone solution to shutdowns.