Coding for Mass Destruction: Cyber-Funded Weaponisation in North Korea
By Larissa Alves Lozano | 3 November 2025
Summary
North Korea state-sponsored actors have weaponised financial phishing, ransomware attacks and cryptocurrency theft to finance military development in the face of strict economic sanctions.
Advancements in cyber attack tactics have evaded economic sanctions and trade embargoes, thus guaranteeing the North Korea regime’s survival and growth.
Financial cyber attacks have the potential to grow in scope through AI tools and modern computing capabilities, which will further fuel weaponisation and the technology race between AI software and cybersecurity systems.
Context
On October 10, 2025, North Korea held a military parade to celebrate the 80th anniversary of its ruling Party. It showcased various new intercontinental ballistic missiles (ICBMs), cruise missiles, and rocket-equipped drone systems. These public displays of power put into question the effect of trade sanctions and embargoes in curtailing North Korea’s military expansion, whose arsenal is vital for its regime survival, according to Kim Jong Un.
A History of Weapons Trade Sanctions
North Korea has a long history of trade restrictions related to its military arsenal. Since 2006, the United Nations Security Council (UNSCR) has imposed nearly a dozen resolutions sanctioning North Korea’s nuclear weapons program and related resources and activities. UNSCR 1718 in 2006 was a response to North Korea’s first nuclear test and sanctioned the trade of heavy weaponry, missile technologies, and other weapon-related materials. Sanctions tightened over time as North Korea continued to test new nuclear weapons. UNSCR 2321 in 2016 banned the export of copper, nickel, silver, and zinc, expanded the restriction on luxury goods, and ordered UN member states to halt accounts and transactions with North Korean banks. Sanctions expanded starting in 2017 also include the freeze of assets of individuals involved in the country’s nuclear program, and broader bans on weapon-related metals and technologies and fuel sources such as oil and natural gas. Additionally, the United States (U.S) has imposed its own unilateral sanctions, re-emphasising UN asset and trade restrictions.
These import and export sanctions are intended to target key materials needed for weaponisation, alongside limiting the regime’s source of foreign revenue through banks and luxury trade. Although estimates vary, since 2017, the Korean Institute of America estimates the regime has lost over USD 2b annually in foreign currency through trade and over USD 1b in capital goods due to sanctions and embargoes. Since North Korea cannot acquire weapons funds through traditional means of trade and financial transactions, the regime has turned to covert cyber attacks.
Financial Cyber Attack History
Since 2017, North Korea has accumulated about USD 3b in cryptocurrency theft, in addition to millions of dollars through fraudulent employment applications in foreign companies and millions from other financially motivated cyber threats targeting foreign banks and other financial institutions.
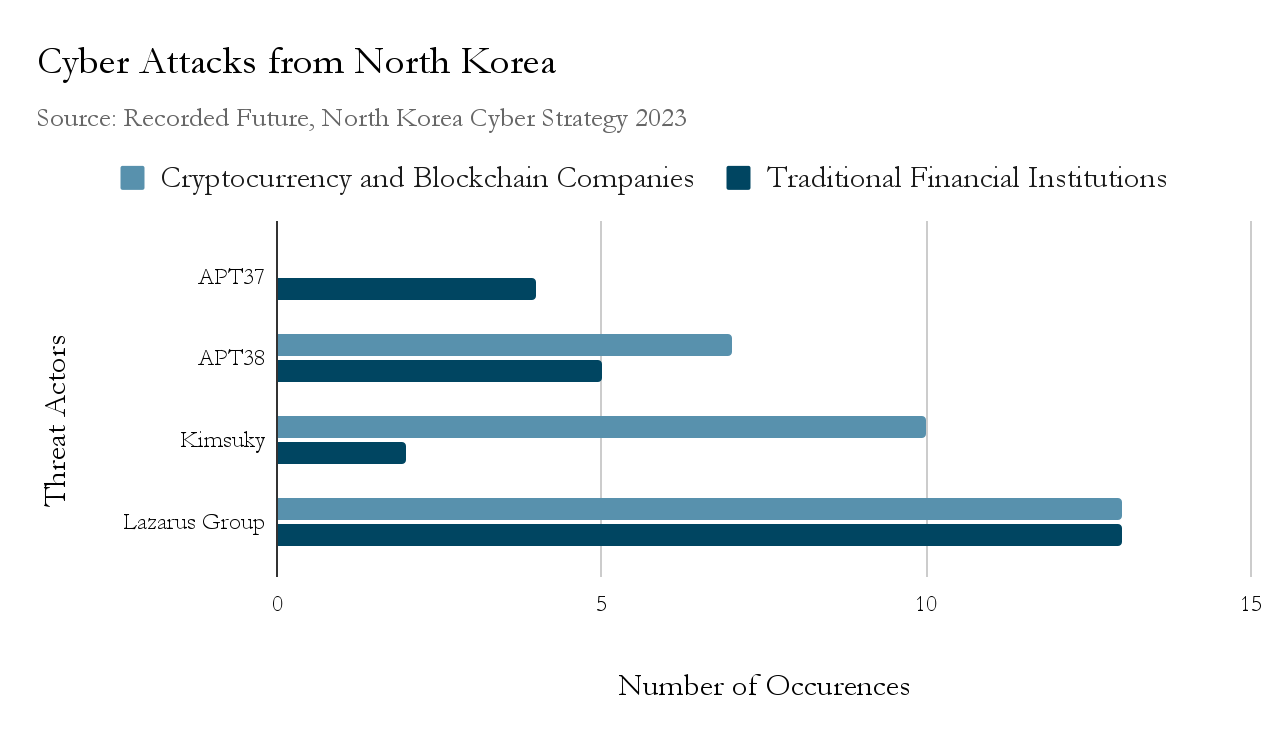
According to a 2024 United Nations report, between 2017 and 2023, North Korea conducted 58 cyberattacks, including the largest cryptocurrency theft in history, worth GBP 1.1b (USD 1.5b). In 2022 alone, North Korean hackers stole about USD 1.35b in cryptocurrency assets. So far in 2025, its crypto theft has reached 2.84b, breaking its record in 2022. The top actors involved in such attacks are APT37, APT38, Kimsuky, and Lazarus Group – the largest North Korean cyber threat actor. APT38 cyberattacks have targeted banks across Bangladesh, Taiwan, South Korea, and Chile, utilising ransomware and spear-phishing techniques to compromise individuals within banks and financial institutions. Lazarus Group has the broadest scope of cyberattack operations and has been active since 2009. It has focused more on targeting cryptocurrency and blockchain companies through ransomware, spear-phishing, and fraudulent profiles; and traditional financial institution attacks through ATM attacks, such as FASTCash and fraudulent accounts.
A 2023 Recorded Future report highlighted various actors involved in North Korean cyberattacks and the primary targets of such attacks. Of the 273 cyberattacks identified, approximately 33 were cryptocurrency-focused, and 26 targeted financial institutions, including foreign banks. Cryptocurrency theft is the second most common cyber threat activity, behind politically motivated attacks targeting government entities. Asia remains the most targeted region by these cyber attacks, but as the regime continues to require more money amidst tightening sanctions, these attacks have expanded to other areas of the world, including the U.S.
Cyber theft has remained a key source of funding for the North Korean military, primarily its missile program, as stated by former U.S. deputy special representative for North Korea Jung Pak. The UN further reports that cyber theft generated approximately 50% of its foreign currency income, accounting for billions of USD from cryptocurrency theft annually, which could fund up to 40% of its nuclear weapons programme.
In addition to targeting banks and cryptocurrency systems, North Korean financial cyberattacks are increasingly focused on fraudulent remote work applications. Recent events have highlighted a growing threat from AI advancements in producing deepfake content within the scope of such operations. Over the years, thousands of remote IT workers across U.S. companies have been discovered to be North Koreans with fraudulent identities by the FBI and the U.S. Justice Department. In August of 2025, North Korean hackers created various false identities utilising Anthropic’s Claude AI for work applications at various US Fortune 500 companies to funnel money to its authoritarian regime. So far, North Korea has sent fraudulent IT workers to eight 8 countries – a sign its cyber money laundering capabilities are expanding beyond Asia-Pacific targets.
Given restrictions regarding direct and indirect transactions by North Korean and most Western actors, North Korea has utilised a network of nearby countries to smuggle its stolen assets to its regime. The US Financial Crimes Enforcement Network has shown North Korea has funnelled millions of USD through banks across China, Singapore, Cambodia, and the Philippines – a major money-laundering location. Operations encompass routing assets in US dollars through foreign bank accounts or converting stolen US dollars or cryptocurrency into local fiat currency to make them less traceable by financial surveillance operations. These cyber financial networks evade UN restrictions on North Koreans earning money abroad. North Korea’s access to VPNs, Chinese-backed IP addresses and IT infrastructure, Russia-provided internet, and cryptocurrency mixer systems such as Sinbad, Tornado Cash, and Blender.io, has allowed North Korea to evade surveillance and transaction tracking across international cash transfer networks and secure funding for its weapons industry.
Analysis and Implications
North Korea has weaponised cyber threats to evade sanction restrictions, which has shocked officials across the United Nations and the U.S. Even with companies banning fraudulent user accounts and immediately taking action to improve their AI detection and cybersecurity systems, North Korean cyber threat actors appear to become more effective every year.
The US Department of Justice seized about USD 7.7m in cryptocurrency assets tied to North Korean fraud, including 280 crypto accounts, and has prosecuted various North Korean and allied Chinese actors involved in large-scale financial theft. Moreover, in June of 2025, the United States Department of Treasury imposed new sanctions on North Korean actors tied to fraudulent IT work targeting operations as an attempt to curtail funds to its weapons programs, with little success given the August attacks using Anthropic’s AI platform. Concerningly, cyber threat actors remain heavily financially motivated and financial gains continue to increase every year as the regime requires more funding for weapons modernisation amidst tightening sanctions.
North Korean cyber tactics have become more elaborate and widespread, and the growing use of AI tools would only exacerbate these concerns. AI could open the door for automation, and advances in generative AI and prompting techniques could lead to novel, sophisticated cyber threats with harder-to-detect fraudulent identities and more complex asset transfers. Until countries take measures to limit access to cryptocurrency platforms and financial transaction systems become more robust against fraudulent VPNs and fraudulent accounts, North Korea's weaponisation will continue to prosper.
Glen Carrie/Unsplash
Forecast
Short-term (Now - 3 months)
If North Korea’s access to cyber theft tactics remains unrestricted, economic sanctions and trade embargoes are highly likely to remain inefficient in curtailing its weapons program, as they do not address cyber financial sources.
AI-enhanced cyber threats will likely fuel the AI technology race, driving financial institutions to improve their cybersecurity infrastructures continuously.
As Chinese-made AI tools become more advanced, it is a realistic possibility that China and North Korea will expand their partnership in financial cyberattacks.
Long-term (>1 year)
The gap between AI capabilities and outdated financial and cryptocurrency trading systems will likely continue to be exploited as cybersecurity measures struggle to keep pace with novel AI cyber threats.
Cyber attack enhancements will likely strengthen cybersecurity infrastructures. However, it will demand extensive quantities of critical minerals to produce advanced computer chips and data centres to store the data to support these systems.